Table of Contents
Introduction
In this guide, we are looking into a PAM implementation. By default, SFTP chroots and non-chroot users’ last login information will not be saved, To get the same we need to configure the PAM.
While the security team looks for each and every log from our server its system admin is responsible to implement the logging system, This guide applies for both RHEL 6 & 7 based operating systems.
Enabling last log information for SFTP users in Red Hat Enterprise Linux and variants.
Check for PAM
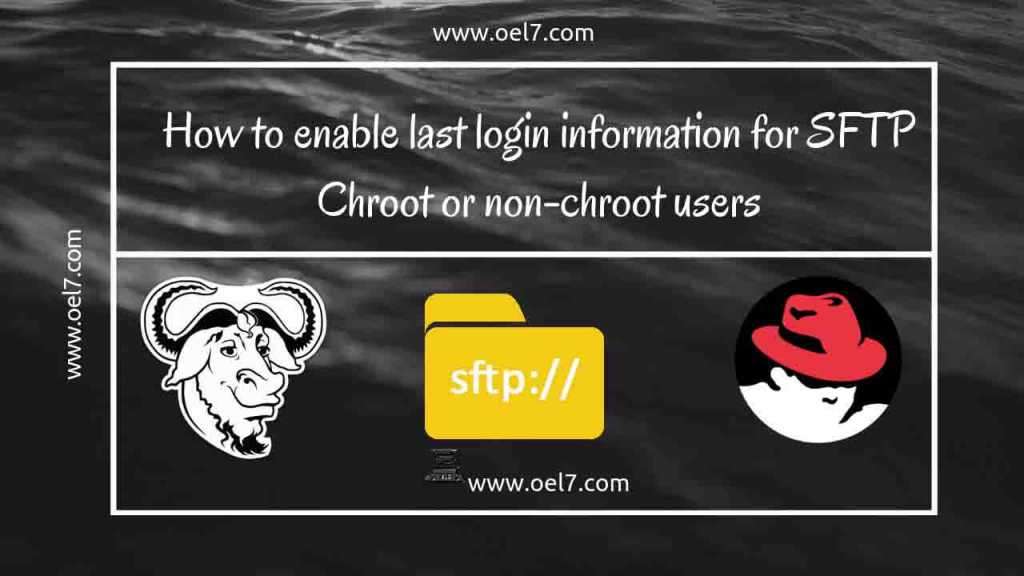
Before starting with implementing PAM let us verify whether the pam module enabled and PAM support enabled in sshd_config using a simple grep.
# grep "pam_lastlog" /etc/pam.d/sshd # grep "UsePAM" /etc/ssh/sshd_config
Enable PAM
Edit and configure the PAM settings to “Yes” in SSHD configuration to start using PAM.
# vi /etc/ssh/sshd_config UsePAM=yes
PAM configuration
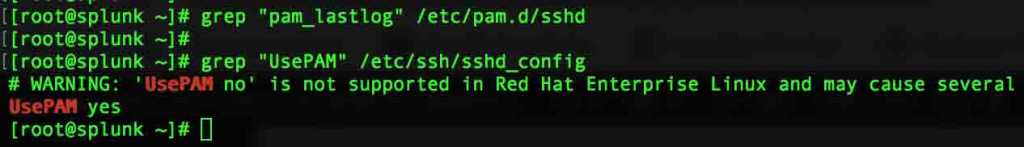
Enable pam_laslog.so by adding in the first line of the session section above the SELinux.
# vi /etc/pam.d/sshd
Add only the first line which contains pam_lastlog.so
session required pam_lastlog.so # Append with only this line. session required pam_selinux.so close session required pam_loginuid.so
Make the changes Effective
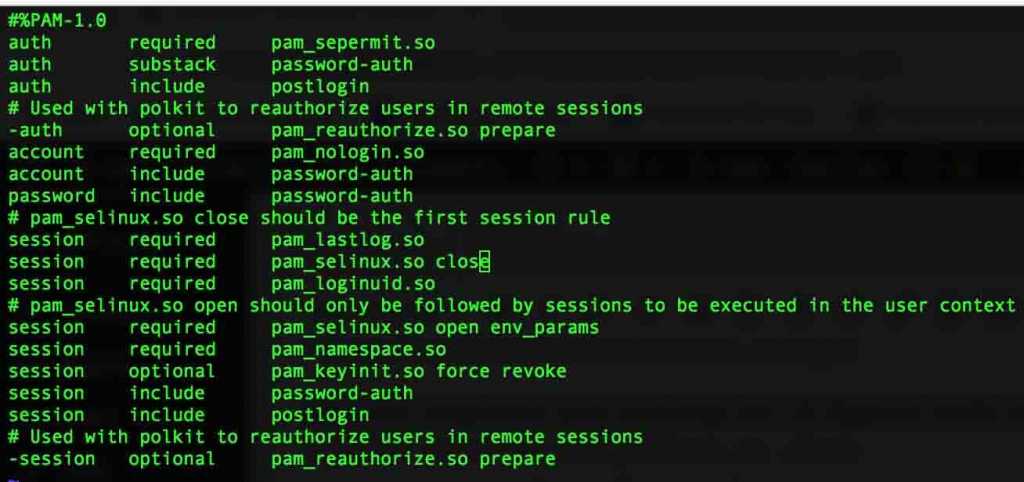
Restart the SSHD service and check for the status.
# systemctl restart sshd # systemctl status sshd
Finally, the last log will start to log all SFTP chroot user and non-chroot user log-in information under the wtmp file.
# lastlog
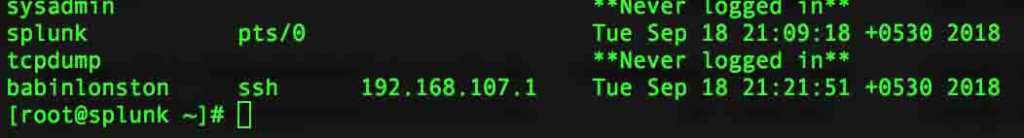
That’s it, We have managed to enable last log information for SFTP Chroot and non-chroot users.
Conclusion:
A default configuration which not in place has been implemented using PAM for chrooting users in RHEL based operating systems. This will help us to find which user accessing the server for the SFTP service, It’s a key factor for security audit purposes.
Provide your feedback in the below comment section we are looking forward to hearing something from you.