Table of Contents
Introduction to Integrating IDM with AD
Integrating IDM with AD (Active Directory) using Indirect cross-forest trust in this guide, we are about to walk through one of the most wanted guides in the real-time production environment.
The scenario as follows, your Active Directory server and DNS are running on a Windows 2012/2016 server. All your windows clients are good to get DNS resolution and user authentication, management from the AD. However, for Linux clients joining to AD have plenty of limitations, So we are setting up IDM server as an intermediator between AD and Linux clients.
By having an IDM server we will get many advantages such as account management, Password policy, Kerberos, RBAC, HBAC, OTP, 2FA, Sudo and much more. If you join a Linux machine to AD using “realm join” you won’t get these features.
In case you have not set up with IDM kindly refer
- Step by step installing an Identity Management server in Linux using IPA
- Creating DNS zones and DNS records in IPA Server
- Setup a Linux server as IDM client to authenticate with Active Directory
Our Current Server Setup
| SERVERS | IP ADDRESSES | HOSTNAMES |
|---|---|---|
| Active Directory | 192.168.107.99 | addns.winlinuxsysadmins.local |
| IDM Server | 192.168.107.100 | idmns.linuxsysadmins.local |
| Clinet1 | 192.168.107.101 | client1.linuxsysadmins.local |
| Clinet2 | 192.168.107.102 | client2.linuxsysadmins.local |
Firewall and Ports
By enabling the firewall and adding the service below are the ports required to set up with an AD trust.
# cat /usr/lib/firewalld/services/freeipa-trust.xml[root@idmns ~]# cat /usr/lib/firewalld/services/freeipa-trust.xml <?xml version="1.0" encoding="utf-8"?> <service> <short>FreeIPA trust setup</short> <description>FreeIPA is an LDAP and Kerberos domain controller for Linux systems. Enable this option of you plan to deploy cross-forest trusts with FreeIPA and Active Directory.</description> <port protocol="tcp" port="135"/> <port protocol="tcp" port="138-139"/> <port protocol="udp" port="138-139"/> <port protocol="tcp" port="389"/> <port protocol="udp" port="389"/> <port protocol="tcp" port="445"/> <port protocol="udp" port="445"/> <port protocol="udp" port="1024-1300"/> <port protocol="tcp" port="3268"/> </service> [root@idmns ~]#
| S:NO: | TCP PORTS | UDP PORTS | USE OF PORT |
|---|---|---|---|
| 1. | 135 | – | epmap |
| 2. | 138-139 | 138-139 | netbios-dgm/netbios-ssn |
| 3. | 389 | 389 | ldap |
| 4. | 445 | 445 | microsoft-ds |
| 5. | – | 1024-1300 | epmap listener range |
| 6. | 3268 | – | msft-gc |
By running firewalld we are good with enabling ports.
# firewall-cmd --add-service=freeipa-trust
# firewall-cmd --reloadTime Configuration
Before starting with any changes first, we need to make sure both IDM server and AD running under the same timezone, syncing with proper date and time.
# systemctl enable chronyd
# systemctl start chronyd
# timedatectl statusVerify the timezone and date in AD as well.
Double-check the DNS of IDM server
Make sure to use the DNS of IDM server with 127.0.0.1. Modify the interface configuration by adding DNS, By the following restart and verify the changes.
# nmcli connection modify ens33 ipv4.dns 127.0.0.1
# ifdown ens33 && ifup ens33
# cat /etc/resolv.confNow it should reflect the changes under the /etc/resolv.conf
[root@idmns ~]# nmcli connection modify ens33 ipv4.dns 127.0.0.1
[root@idmns ~]#
[root@idmns ~]# ifdown ens33 && ifup ens33
Device 'ens33' successfully disconnected.
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/2)
[root@idmns ~]#
[root@idmns ~]# cat /etc/resolv.conf
Generated by NetworkManager
search linuxsysadmins.local
nameserver 127.0.0.1
[root@idmns ~]#In case if you update the DNS it’s required to restart the following services krb5kdc, sssd, httpd to take effect.
# systemctl restart krb5kdc.service
# systemctl restart sssd.service
# systemctl restart httpd.service
# ipactl statusInstalling trust Packages
In Case, the ad-trust package is not installed its time to start with installing, else skip to next steps.
# yum install ipa-server-trust-ad -yThe version of IPA we are using is 4.6.4 some of the commands for lower versions differ from this guide.
[root@idmns ~]# ipa --version
VERSION: 4.6.4, API_VERSION: 2.229
[root@idmns ~]#Configure IDM for Cross-forest Trust
Before starting with running the further commands we need to know the current NetBIOS name. Navigate to IDM server GUI under IPA Server –> Trusts –> Global Trust Configuration
# ipa-adtrust-install --netbios-name=LINUXSYS -a redhat123- ipa-server-install – Command to set up the AD trust.
- –netbios-name – Name of Netbios we used during IDM setup.
- -a – Admin Password
[root@idmns ~]# ipa-adtrust-install --netbios-name=LINUXSYSADMINS -a redhat123
The log file for this installation can be found in /var/log/ipaserver-install.log
This program will setup components needed to establish trust to AD domains for
the IPA Server.
This includes:
Configure Samba
Add trust related objects to IPA LDAP server
To accept the default shown in brackets, press the Enter key.
IPA generated smb.conf detected.
Overwrite smb.conf? [no]: yes
Do you want to enable support for trusted domains in Schema Compatibility plugin?
This will allow clients older than SSSD 1.9 and non-Linux clients to work with trusted users.
Enable trusted domains support in slapi-nis? [no]: yes
The following operations may take some minutes to complete.
Please wait until the prompt is returned.
Configuring CIFS
[1/23]: validate server hostname
[2/23]: stopping smbd
[3/23]: creating samba domain object
Samba domain object already exists
[4/23]: creating samba config registry
[5/23]: writing samba config file
[6/23]: adding cifs Kerberos principal
[7/23]: adding cifs and host Kerberos principals to the adtrust agents group
[8/23]: check for cifs services defined on other replicas
[9/23]: adding cifs principal to S4U2Proxy targets
cifs principal already targeted, nothing to do.
[10/23]: adding admin(group) SIDs
Admin SID already set, nothing to do
Admin group SID already set, nothing to do
[11/23]: adding RID bases
RID bases already set, nothing to do
[12/23]: updating Kerberos config
'dns_lookup_kdc' already set to 'true', nothing to do.
[13/23]: activating CLDAP plugin
CLDAP plugin already configured, nothing to do
[14/23]: activating sidgen task
Sidgen task plugin already configured, nothing to do
[15/23]: configuring smbd to start on boot
[16/23]: adding special DNS service records
[17/23]: enabling trusted domains support for older clients via Schema Compatibility plugin
[18/23]: restarting Directory Server to take MS PAC and LDAP plugins changes into account
[19/23]: adding fallback group
Fallback group already set, nothing to do
[20/23]: adding Default Trust View
Default Trust View already exists.
[21/23]: setting SELinux booleans
[22/23]: starting CIFS services
[23/23]: restarting smbd
Done configuring CIFS.
=============================================================================
Setup complete
You must make sure these network ports are open:
TCP Ports:
* 135: epmap
* 138: netbios-dgm
* 139: netbios-ssn
* 445: microsoft-ds
* 1024..1300: epmap listener range
* 3268: msft-gc
UDP Ports:
* 138: netbios-dgm
* 139: netbios-ssn
* 389: (C)LDAP
* 445: microsoft-ds
See the ipa-adtrust-install(1) man page for more details
=============================================================================
[root@idmns ~]# Once we are done with setting up ad-trust you will get to know what are the ports need to be enabled in between AD and IDM. We can ignore this step because it’s already done in our firewall step.
DNS configuration for Active Directory (AD) and IDM
1. Creating DNS conditional forwarder on AD
Take a cmd prompt with Administrator privilege and run the below command to enable the conditional forwarders for IDM server under Active Directory.
dnscmd 127.0.0.1 /ZoneAdd linuxsysadmins.local /Forwarder 192.168.107.100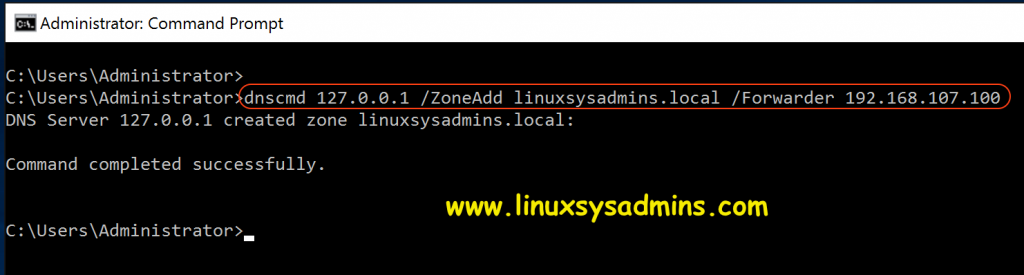
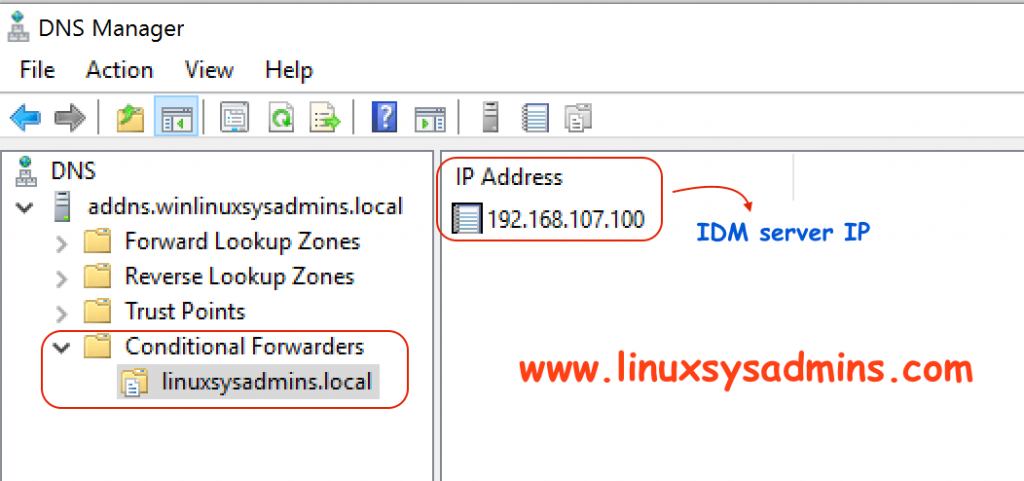
The above command will add a conditional forwarder under DNS Manager.
Service Manager –> DNS –> DNS Manager
2. Creating DNS forwarder on IDM
The DNS resolution from any Linux clients with IDM server should forward the request to Active Directory for that we need to add a DNS forwarder only policy in IDM by pointing to AD server’s IP address.
# ipa dnsforwardzone-add winlinuxsysadmins.local --forwarder=192.168.107.99 --forward-policy=only[root@idmns ~]# ipa dnsforwardzone-add winlinuxsysadmins.local --forwarder=192.168.107.99 --forward-policy=only
Server will check DNS forwarder(s).
This may take some time, please wait …
ipa: WARNING: DNS server 192.168.107.99: query 'winlinuxsysadmins.local. SOA': The DNS response does not contain an answer to the question: winlinuxsysadmins.local. IN SOA.
Zone name: winlinuxsysadmins.local.
Active zone: TRUE
Zone forwarders: 192.168.107.99
Forward policy: only
[root@idmns ~]#To verify the same from GUI navigate under Network –> DNS –> DNS Forward Zones
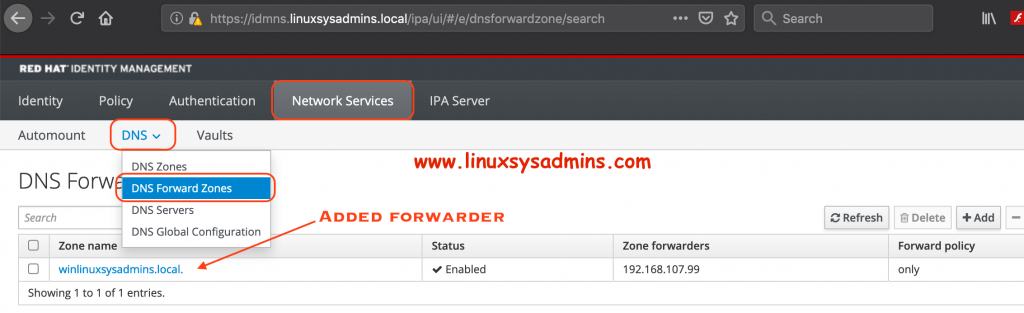
Adding from GUI too easier. however, in a single command, we can create this entry.
Verifying DNS configuration on AD and IDM
Verify DNS on the AD server
To verify the DNS configuration in AD launch a CMD prompt and start with looking for nslookup. Set the Service record (SRV) as the type and do a query. We should get the Answer section as expected to confirm DNS works perfectly.
nslookup
> set type=srv
> _ldap._tcp.winlinuxsysadmins.local
> _ldap._tcp.linuxsysadmins.local
exit 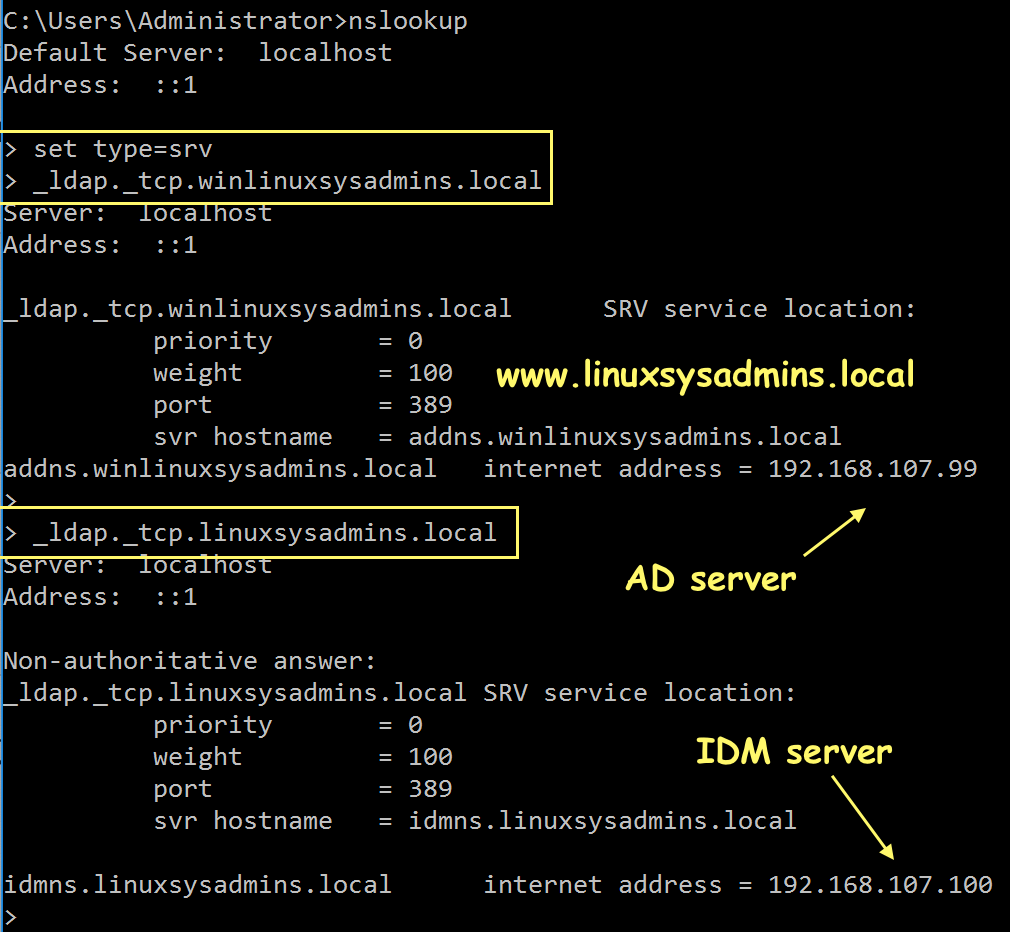
Check the DNS on IDM Server
# dig SRV _ldap._tcp.linuxsysadmins.local
# dig SRV _ldap._tcp.winlinuxsysadmins.local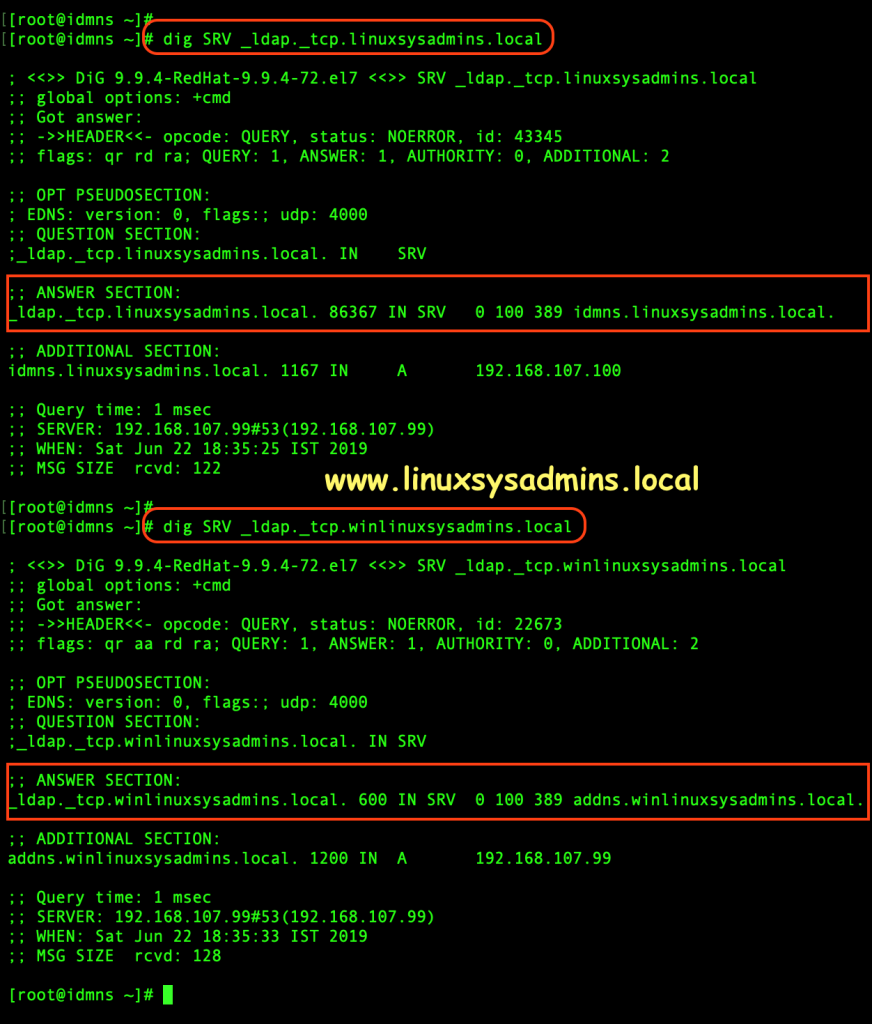
Disable DNS Validation
# vim /etc/named.conf
# dnssec-validation no;Click on right side NEXT to continue reading
Establishing trust with AD Domain
We can accomplish the trust by two methods. By running “trust-add” and enter the Admin password or using the secret method. Here we are using the “trust-add” method.
Once we run, the trusts relationship to “winlinuxsysadmins.local” will become ‘trusted’. It will prompt to enter the “Administrator” account password of the AD server.
# ipa trust-add --type=ad winlinuxsysadmins.local --admin Administrator --password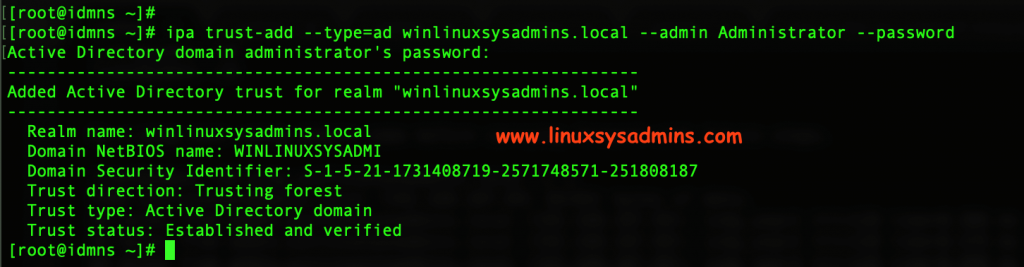
Now, IPA has created one-way forest trust on the IDM side. We have completed with a one-way trust. To verify from GUI navigate to IPA Server –> Trusts as shown in below picture.
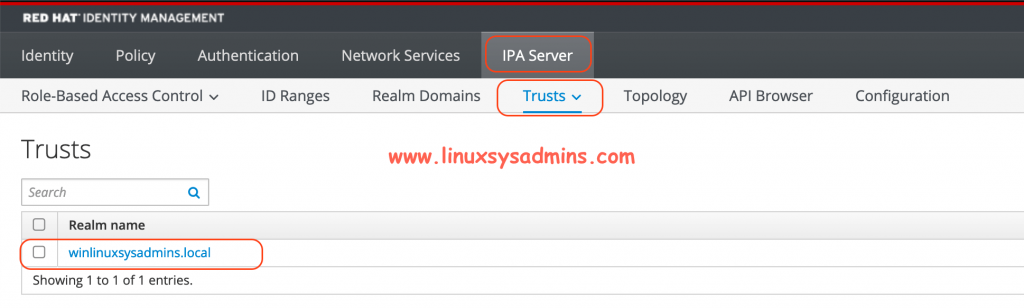
By clicking on it will give more information about the windows trust.
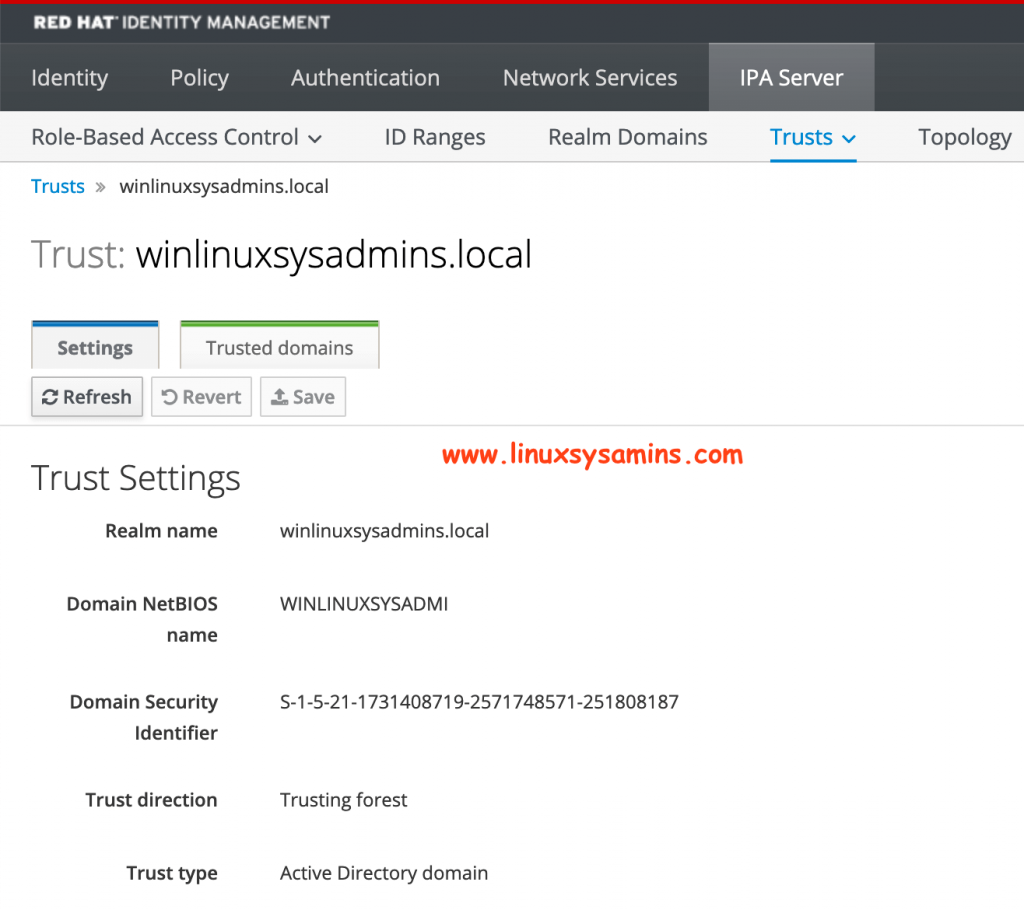
Using Secret method
The above method can be followed or we have an alternative method using a secret. By using this method we don’t need to enter the Admin password. This will help in case we don’t have the Administrator access to the AD.
# ipa trust-add winlinuxsysadmins.local --trust-secretCreating Trust in Active Directory
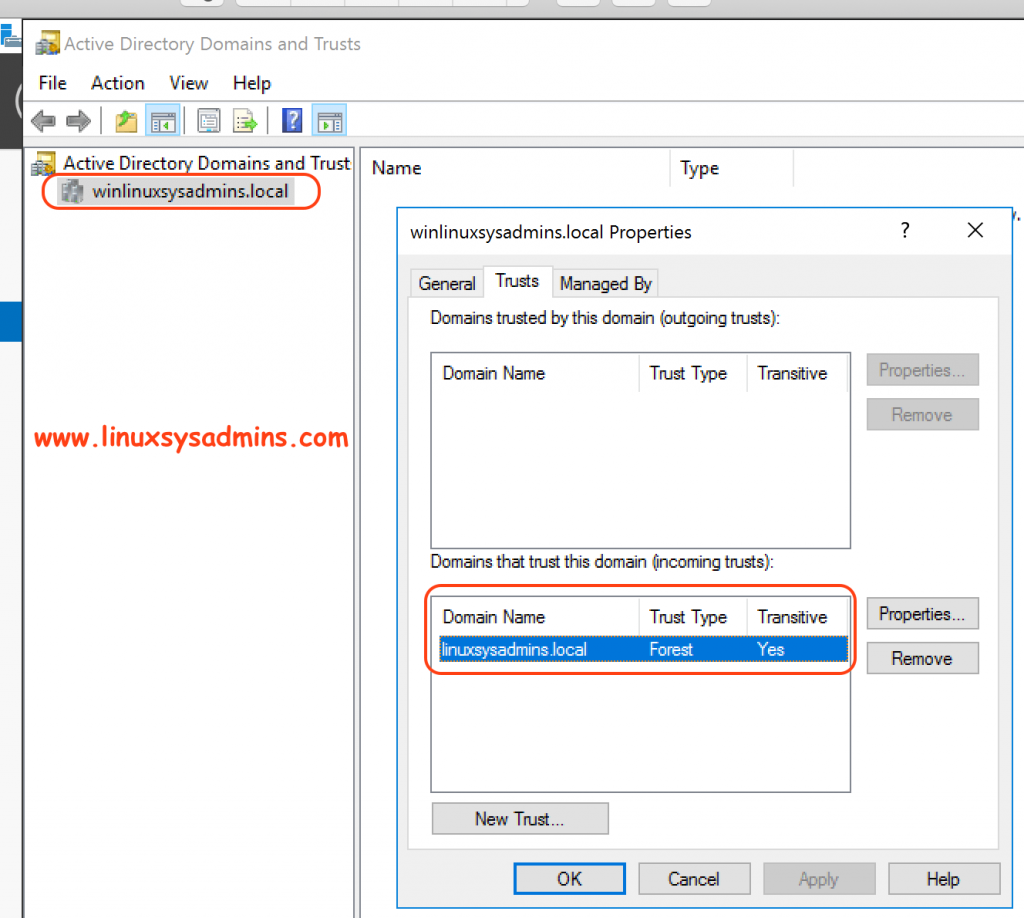
Then switch to Windows side and start creating trust, refer below snip.
In DNS Server Service Manager –> AD DS –> Active Directory Domains and Trust –> Right Click –> Properties –> Trust TAB –> “Domain that trust this domain (incoming trusts) { This will be already exists} –> Refresh
Note:> Here we need to keep in mind, only IDM needs to trust the AD for resolving all incoming request.
Fetch and find the trusted domain on IDM
Once the “linuxsyadmins.local” trusted by AD try to retrieve the list of trusted forest domain from the Active Directory.
# ipa trust-fetch-domains "winlinuxsysadmins.local"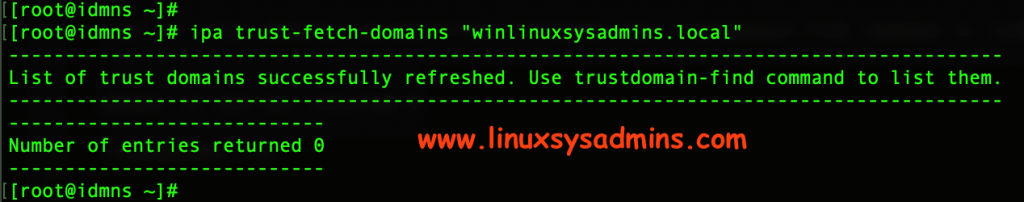
Find the “winlinuxsysadmins.local” now we should get the domain information as follow.
# ipa trustdomain-find "winlinuxsysadmins.local"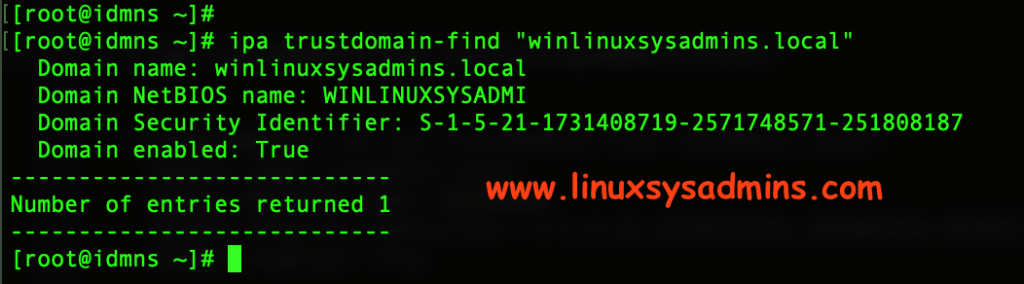
To show all the available trust information we can use trust-show –all option with IPA command.
# ipa trust-show --allOutput for your reference
[root@idmns ~]# ipa trust-show --all
Realm name: winlinuxsysadmins.local
dn: cn=winlinuxsysadmins.local,cn=ad,cn=trusts,dc=linuxsysadmins,dc=local
Realm name: winlinuxsysadmins.local
Domain NetBIOS name: WINLINUXSYSADMI
Domain Security Identifier: S-1-5-21-1731408719-2571748571-251808187
SID blacklist incoming: S-1-0, S-1-1, S-1-2, S-1-3, S-1-5-1, S-1-5-2, S-1-5-3, S-1-5-4, S-1-5-5, S-1-5-6, S-1-5-7, S-1-5-8, S-1-5-9, S-1-5-10, S-1-5-11, S-1-5-12, S-1-5-13,
S-1-5-14, S-1-5-15, S-1-5-16, S-1-5-17, S-1-5-18, S-1-5-19, S-1-5-20
SID blacklist outgoing: S-1-0, S-1-1, S-1-2, S-1-3, S-1-5-1, S-1-5-2, S-1-5-3, S-1-5-4, S-1-5-5, S-1-5-6, S-1-5-7, S-1-5-8, S-1-5-9, S-1-5-10, S-1-5-11, S-1-5-12, S-1-5-13,
S-1-5-14, S-1-5-15, S-1-5-16, S-1-5-17, S-1-5-18, S-1-5-19, S-1-5-20
Trust direction: Trusting forest
Trust type: Active Directory domain
gidnumber: 5001
ipantsecurityidentifier: S-1-5-21-479538025-3999940732-1828893943-1003
ipantsupportedencryptiontypes: 28
ipanttrustauthincoming: AQAAAAwAAAAcAQAAgElEMuUm1QECAAAAAAEAAGUAMwAyAEYAOAAhAGoAWAAyAEwAKABVADQALAAkADAAPwBtADMAOQBfAHUAbwBrAEAAYQA5AGMAUwAuAHUAagApADYALAA6AGYAPABQAEoAZgBEAEEAcQBHAGIAeABQAG4ANwBhAEUAeAAyAEMAZABLAE8AagA9ACYAfgB1AE0AXQBbAE4AdAA9ADsATgBGAGcAcwBAACYARQBaAHIAawAyAE4AdgBBAGkAbABJAFkAQABLAFYALQBjAHIATgBSAFsARgBLAFYANQBCADwAOwBuAFoAUQBqAGMAKAAuAG4ASQBPAGkAPgA9AFsASgBCAHUAdQAwACkAVwBwAFsAdwCASUQy5SbVAQIAAAAAAQAAZQAzADIARgA4ACEAagBYADIATAAoAFUANAAsACQAMAA/AG0AMwA5AF8AdQBvAGsAQABhADkAYwBTAC4AdQBqACkANgAsADoAZgA8AFAASgBmAEQAQQBxAEcAYgB4AFAAbgA3AGEARQB4ADIAQwBkAEsATwBqAD0AJgB+AHUATQBdAFsATgB0AD0AOwBOAEYAZwBzAEAAJgBFAFoAcgBrADIATgB2AEEAaQBsAEkAWQBAAEsAVgAtAGMAcgBOAFIAWwBGAEsAVgA1AEIAPAA7AG4AWgBRAGoAYwAoAC4AbgBJAE8AaQA+AD0AWwBKAEIAdQB1ADAAKQBXAHAAWwB3AA==
ipanttrustauthoutgoing: AQAAAAwAAAAcAQAAgElEMuUm1QECAAAAAAEAAGUAMwAyAEYAOAAhAGoAWAAyAEwAKABVADQALAAkADAAPwBtADMAOQBfAHUAbwBrAEAAYQA5AGMAUwAuAHUAagApADYALAA6AGYAPABQAEoAZgBEAEEAcQBHAGIAeABQAG4ANwBhAEUAeAAyAEMAZABLAE8AagA9ACYAfgB1AE0AXQBbAE4AdAA9ADsATgBGAGcAcwBAACYARQBaAHIAawAyAE4AdgBBAGkAbABJAFkAQABLAFYALQBjAHIATgBSAFsARgBLAFYANQBCADwAOwBuAFoAUQBqAGMAKAAuAG4ASQBPAGkAPgA9AFsASgBCAHUAdQAwACkAVwBwAFsAdwCASUQy5SbVAQIAAAAAAQAAZQAzADIARgA4ACEAagBYADIATAAoAFUANAAsACQAMAA/AG0AMwA5AF8AdQBvAGsAQABhADkAYwBTAC4AdQBqACkANgAsADoAZgA8AFAASgBmAEQAQQBxAEcAYgB4AFAAbgA3AGEARQB4ADIAQwBkAEsATwBqAD0AJgB+AHUATQBdAFsATgB0AD0AOwBOAEYAZwBzAEAAJgBFAFoAcgBrADIATgB2AEEAaQBsAEkAWQBAAEsAVgAtAGMAcgBOAFIAWwBGAEsAVgA1AEIAPAA7AG4AWgBRAGoAYwAoAC4AbgBJAE8AaQA+AD0AWwBKAEIAdQB1ADAAKQBXAHAAWwB3AA==
ipanttrustpartner: winlinuxsysadmins.local
ipanttrustposixoffset: 0
objectclass: ipaNTTrustedDomain, ipaIDobject, top
uidnumber: 5003
[root@idmns ~]# Or to get only our added trust information to specify with a domain name by the following command.
# ipa trust-show winlinuxsysadmins.localLess information for trust as shown below.
[root@idmns ~]# ipa trust-show winlinuxsysadmins.local
Realm name: winlinuxsysadmins.local
Domain NetBIOS name: WINLINUXSYSADMI
Domain Security Identifier: S-1-5-21-1731408719-2571748571-251808187
Trust direction: Trusting forest
Trust type: Active Directory domain
[root@idmns ~]#Verify AD admin privilege accounts on IDM
Almost most of the configurations are done let obtain a Kerberos ticket for win domains Administrator account. Enter the Administrator account password when prompt.
# kinit Administrator@winlinuxsysadmins.localOutput for your reference
[root@idmns ~]# kinit Administrator@winlinuxsysadmins.local
Password for Administrator@winlinuxsysadmins.local:
[root@idmns ~]#List the obtained Kerberos ticket using klist command, Here we can find the Administrator has a valid kb ticket.
[root@idmns ~]# klist
Ticket cache: KEYRING:persistent:0:krb_ccache_QKwQFhc
Default principal: Administrator@WINLINUXSYSADMINS.LOCAL
Valid starting Expires Service principal
06/20/19 03:45:21 06/20/19 13:45:21 krbtgt/WINLINUXSYSADMINS.LOCAL@WINLINUXSYSADMINS.LOCAL
renew until 06/21/19 03:45:17
[root@idmns ~]#Creating external Groups on IDM
To import all users from trusted AD to IDM we need to create external groups.
# ipa group-add --desc='WINLINUXSYSADMINS.local admins external map' winlinuxsysadmins.local_external --external
# ipa group-add --desc='WINLINUXSYSADMINS.local admins' winlinuxsysadmins.localAdding Users to an external group
Once completed with group add all the users to existing external group from the trusted domain by entering the null value while asking for user/group.
# ipa group-add-member WINLINUXSYSADMINS.local_external --external 'WINLINUXSYSADMINS\Domain Admins'Leave user and group blank, Just press enter.
Verify all Accounts
Now it’s time to verify all accounts using “getent” command with option and argument by replacing our win domain.
# getent passwd Administrator@winlinuxsysadmins.local
# getent passwd babin@winlinuxsysadmins.local
# getent passwd lonston@winlinuxsysadmins.localBelow output for your reference
[root@idmns ~]# getent passwd Administrator@winlinuxsysadmins.local
administrator@winlinuxsysadmins.local:*:916000500:916000500:Administrator:/home/winlinuxsysadmins.local/administrator:
[root@idmns ~]#
[root@idmns ~]# getent passwd babin@winlinuxsysadmins.local
babin@winlinuxsysadmins.local:*:916001104:916001104:Bobin L.:/home/winlinuxsysadmins.local/babin:
[root@idmns ~]#
[root@idmns ~]# getent passwd lonston@winlinuxsysadmins.local
lonston@winlinuxsysadmins.local:*:916001105:916001105:Lonston L.:/home/winlinuxsysadmins.local/lonston:Adding external group to POSIX group
Now we required to allow admin users of “winlinuxsysadmins.local_external” with POSIX group.
# ipa group-add-member WINLINUXSYSADMINS.LOCAL --groups WINLINUXSYSADMINS.local_externalOutput for reference
# ipa group-add-member WINLINUXSYSADMINS.LOCAL --groups WINLINUXSYSADMINS.local_external
[root@idmns ~]# ipa group-add-member WINLINUXSYSADMINS.LOCAL --groups WINLINUXSYSADMINS.local_external
Group name: winlinuxsysadmins.local
Description: WINLINUXSYSADMINS.local admins
GID: 5004
Member groups: winlinuxsysadmins.local_external
Number of members added 1That’s it now let’s verify the accounts.
Verify AD account logins
Quickly do an SSH and verify for all your AD accounts from IDM server.
# ssh babin@winlinuxsysadmins.local@192.168.107.100SSH Session Successful.
[root@idmns ~]# ssh babin@winlinuxsysadmins.local@192.168.107.100
Password:
Last login: Thu Jun 20 14:14:21 2019 from idmns.linuxsysadmins.local
-sh-4.2$
-sh-4.2$ ls -lthra
total 16K
drwx--x--x 3 root root 19 Jun 20 14:13 ..
-rw------- 1 babin@winlinuxsysadmins.local babin@winlinuxsysadmins.local 193 Jun 20 14:13 .bash_profile
-rw------- 1 babin@winlinuxsysadmins.local babin@winlinuxsysadmins.local 18 Jun 20 14:13 .bash_logout
-rw------- 1 babin@winlinuxsysadmins.local babin@winlinuxsysadmins.local 231 Jun 20 14:13 .bashrc
drwx------ 2 babin@winlinuxsysadmins.local babin@winlinuxsysadmins.local 83 Jun 20 14:14 .
-rw------- 1 babin@winlinuxsysadmins.local babin@winlinuxsysadmins.local 45 Jun 20 14:14 .bash_history
-sh-4.2$That’s it we are good with all the above steps according to SSH sessions worked. Hence, this guide is too long in our upcoming guide, we will cover with the client setup.
By following below URL, Start setting up Client-side configuration
Setup a Linux server as IDM client to authenticate with Active Directory
Conclusion
Integrating IDM with AD cross-forest trust setup using IDM has a lot of features, will cover up with more topics on IDM. Your comments are most welcome, in case any update/improvement required in topic kindly let us know through comments. Subscribe to our newsletter to stay with us for more nix guides.
Hi,
To the point post but does not address another nonSSO case using SSH only.
That is a client with hostname under the winlinuxsysadmins.local domain (let us call it c1.winlinuxsysadmins.local) to which the AD users would like to log into.
SSO is out of mind (as the kdc is not within the idm realm), but ssh should still work.
So `ssh ad-user1@winlinuxsysadmins.local@c1.winlinuxsysadmins.local) theoretically would request PAM authentication using sssd from IdM.
However in practice this is not the case.
Any feedback?
Best regaerds
Theo
Hi Babin,
Our requirement is Active Directory groups are not supposed to be displayed on the IDM clients.
Three external groups are created in Redhat IDM(3000,4000,5000). Trust is established between with Active Directory to Redhat IDM with these external groups. Mapping UserID and Group Membership as in IDM View and AD Membership .We have issues seeing all the group memberships in AD on the client-side. We need to restrict ONLY the Unix Groups to be visible to the clients..please guide us
please guide us.
Hi Babin
Can you please help me understand the below regarding the below commands:
# ipa group-add –desc=’WINLINUXSYSADMINS.local admins external map’ winlinuxsysadmins.local_external –external
# ipa group-add –desc=’WINLINUXSYSADMINS.local admins’ winlinuxsysadmins.local
1. Should the group “winlinuxsysadmins.local” have Administrator permissions in AD? Is it a problem if the group has non-Administrator permissions?
2. Is the group “winlinuxsysadmins.local” used for managing AD users in IDM?
Kind regards
Managed to figure out the answers to this:
1. No need for Administrator permissions
2. No
This is a great article. Useful and came in handy for a project I am involved in. Thank yiu.
Hi Ejay,
Glad to know this helped you.
Thanks & Regards,
Babin Lonston