Table of Contents
Introduction
In our previous guide setting up a cross-forest trust has been elaborated. By following we are continuing with client setup in IDM series.
Let’s walk through all required steps to accomplish a successful client and server communication using IDM cross-forest trust.
The steps we are going to follow in this guide is as follows.
- Configure Firewall
- Installing Package
- Configuring static IP for IDM client
- Verify DNS
- Run client setup
- Verify accounts
- Login and confirm AD accounts
IDM Client-Server Info
| IP Address | Hostname |
|---|---|
| 192.168.107.101 | client1.linuxsysadmins.local |
| 192.168.107.102 | client2.linuxsysadmins.local |
| 192.168.107.160 | client2.winlinuxsysadmins.local |
Firewall for IDM Clients
By default, RHEL, CentOS, Oracle Linux are not coming with free IPA clients services for firewall so let’s create one and use it.
Create a firewall service XML under below location
# vim /usr/lib/firewalld/services/freeipa-clients.xml[root@vcs1 ~]# cat /usr/lib/firewalld/services/freeipa-clients.xml <?xml version="1.0" encoding="utf-8"?> <service> <short>FreeIPA Client</short> <description>FreeIPA Clients Required Ports.</description> <port protocol="tcp" port="80"/> <port protocol="tcp" port="88"/> <port protocol="tcp" port="389"/> <port protocol="udp" port="88"/> <port protocol="tcp" port="464"/> <port protocol="udp" port="464"/> <port protocol="udp" port="123"/> </service>
Once service XML created reload the firewall-cmd, By following permanently add the freeIPA client’s service and reload the firewall to take effect.
# firewall-cmd --reload
# firewall-cmd --add-service=freeipa-clients --permanent
# firewall-cmd --reload
# firewall-cmd --list-all[root@client1 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: ens33
sources:
services: ssh dhcpv6-client freeipa-clients
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
[root@client1 ~]#Installing IDM Client Package
Now it’s time to install the client package, by running the yum install will pull down all required dependencies and install the client.
# yum install ipa-client -yInstalled:
ipa-client.x86_64 0:4.6.4-10.el7
Dependency Installed:
autofs.x86_64 1:5.0.7-99.el7 autogen-libopts.x86_64 0:5.18-5.el7 avahi-libs.x86_64 0:0.6.31-19.el7
c-ares.x86_64 0:1.10.0-3.el7 certmonger.x86_64 0:0.78.4-10.el7 cups-libs.x86_64 1:1.6.3-35.el7
cyrus-sasl-gssapi.x86_64 0:2.1.26-23.el7 gssproxy.x86_64 0:0.7.0-21.el7 hesiod.x86_64 0:3.2.1-3.el7
http-parser.x86_64 0:2.7.1-5.el7_4 ipa-client-common.noarch 0:4.6.4-10.el7 ipa-common.noarch 0:4.6.4-10.el7
keyutils.x86_64 0:1.5.8-3.el7 krb5-workstation.x86_64 0:1.15.1-34.el7 libbasicobjects.x86_64 0:0.1.1-32.el7
libcollection.x86_64 0:0.7.0-32.el7 libdhash.x86_64 0:0.5.0-32.el7 libevent.x86_64 0:2.0.21-4.el7
libini_config.x86_64 0:1.3.1-32.el7 libipa_hbac.x86_64 0:1.16.2-13.el7 libkadm5.x86_64 0:1.15.1-34.el7
libldb.x86_64 0:1.3.4-1.el7 libnfsidmap.x86_64 0:0.25-19.el7 libpath_utils.x86_64 0:0.2.1-32.el7
libref_array.x86_64 0:0.1.5-32.el7 libsmbclient.x86_64 0:4.8.3-4.el7 libsss_autofs.x86_64 0:1.16.2-13.el7
libsss_certmap.x86_64 0:1.16.2-13.el7 libsss_idmap.x86_64 0:1.16.2-13.el7 libsss_nss_idmap.x86_64 0:1.16.2-13.el7
libsss_sudo.x86_64 0:1.16.2-13.el7 libtalloc.x86_64 0:2.1.13-1.el7 libtdb.x86_64 0:1.3.15-1.el7
libtevent.x86_64 0:0.9.36-1.el7 libtirpc.x86_64 0:0.2.4-0.15.el7 libverto-tevent.x86_64 0:0.2.5-4.el7
libwbclient.x86_64 0:4.8.3-4.el7 nfs-utils.x86_64 1:1.3.0-0.61.el7 ntp.x86_64 0:4.2.6p5-28.el7
ntpdate.x86_64 0:4.2.6p5-28.el7 oddjob.x86_64 0:0.31.5-4.el7 oddjob-mkhomedir.x86_64 0:0.31.5-4.el7
psmisc.x86_64 0:22.20-15.el7 python-cffi.x86_64 0:1.6.0-5.el7 python-chardet.noarch 0:2.2.1-1.el7_1
python-dns.noarch 0:1.12.0-4.20150617git465785f.el7 python-enum34.noarch 0:1.0.4-1.el7 python-gssapi.x86_64 0:1.2.0-3.el7
python-idna.noarch 0:2.4-1.el7 python-jwcrypto.noarch 0:0.4.2-1.el7 python-ldap.x86_64 0:2.4.15-2.el7
python-libipa_hbac.x86_64 0:1.16.2-13.el7 python-netaddr.noarch 0:0.7.5-9.el7 python-netifaces.x86_64 0:0.10.4-3.el7
python-nss.x86_64 0:0.16.0-3.el7 python-ply.noarch 0:3.4-11.el7 python-pycparser.noarch 0:2.14-1.el7
python-qrcode-core.noarch 0:5.0.1-1.el7 python-requests.noarch 0:2.6.0-1.el7_1 python-sss-murmur.x86_64 0:1.16.2-13.el7
python-sssdconfig.noarch 0:1.16.2-13.el7 python-urllib3.noarch 0:1.10.2-5.el7 python-yubico.noarch 0:1.2.3-1.el7
python2-cryptography.x86_64 0:1.7.2-2.el7 python2-ipaclient.noarch 0:4.6.4-10.el7 python2-ipalib.noarch 0:4.6.4-10.el7
python2-pyasn1.noarch 0:0.1.9-7.el7 python2-pyasn1-modules.noarch 0:0.1.9-7.el7 pyusb.noarch 0:1.0.0-0.11.b1.el7
quota.x86_64 1:4.01-17.el7 quota-nls.noarch 1:4.01-17.el7 rpcbind.x86_64 0:0.2.0-47.el7
samba-client-libs.x86_64 0:4.8.3-4.el7 samba-common.noarch 0:4.8.3-4.el7 samba-common-libs.x86_64 0:4.8.3-4.el7
sssd.x86_64 0:1.16.2-13.el7 sssd-ad.x86_64 0:1.16.2-13.el7 sssd-client.x86_64 0:1.16.2-13.el7
sssd-common.x86_64 0:1.16.2-13.el7 sssd-common-pac.x86_64 0:1.16.2-13.el7 sssd-ipa.x86_64 0:1.16.2-13.el7
sssd-krb5.x86_64 0:1.16.2-13.el7 sssd-krb5-common.x86_64 0:1.16.2-13.el7 sssd-ldap.x86_64 0:1.16.2-13.el7
sssd-proxy.x86_64 0:1.16.2-13.el7 tcp_wrappers.x86_64 0:7.6-77.el7 xmlrpc-c.x86_64 0:1.32.5-1905.svn2451.el7
xmlrpc-c-client.x86_64 0:1.32.5-1905.svn2451.el7
Complete!
[root@client1 ~]#There will be a lot of dependencies for IPA-client, Make sure to use a yum repository.
Configure static IP address
In our setup we are using static IP, so we have configured as follows. Use the IDM server’s IP 192.168.107.100 as DNS IP of all client servers.
[root@client1 ~]# cat /etc/sysconfig/network-scripts/ifcfg-ens33
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=none
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
NAME=ens33
UUID=6aff4d6b-6b32-4166-8953-6429853badec
DEVICE=ens33
ONBOOT=yes
IPADDR=192.168.107.101
PREFIX=24
GATEWAY=192.168.107.2
DNS1=192.168.107.100
DOMAIN=linuxsysadmins.localVerify DNS by cat the resolv.conf
[root@client1 ~]# cat /etc/resolv.conf
Generated by NetworkManager
search linuxsysadmins.local
nameserver 192.168.107.100
[root@client1 ~]#Or verify using dig command
# dig linuxsysadmins.local @192.168.107.100
# dig -x 192.168.107.100Run Client setup
Start to set up the client by running “ipa-client-install” command with options and argument.
# ipa-client-install --enable-dns-updates --force-ntpd --mkhomedir
or
# ipa-client-install --domain linuxsysadmins.local --server idmns.linuxsysadmins.local --realm LINUXSYSADMINS.LOCAL- ipa-client-install – Command to run the client setup.
- –enable-dns-updates – To get the DNS information.
- –force-ntpd – Force to get the time from IDM server.
- –mkhomedir – Create the user’s home directory on their first login.
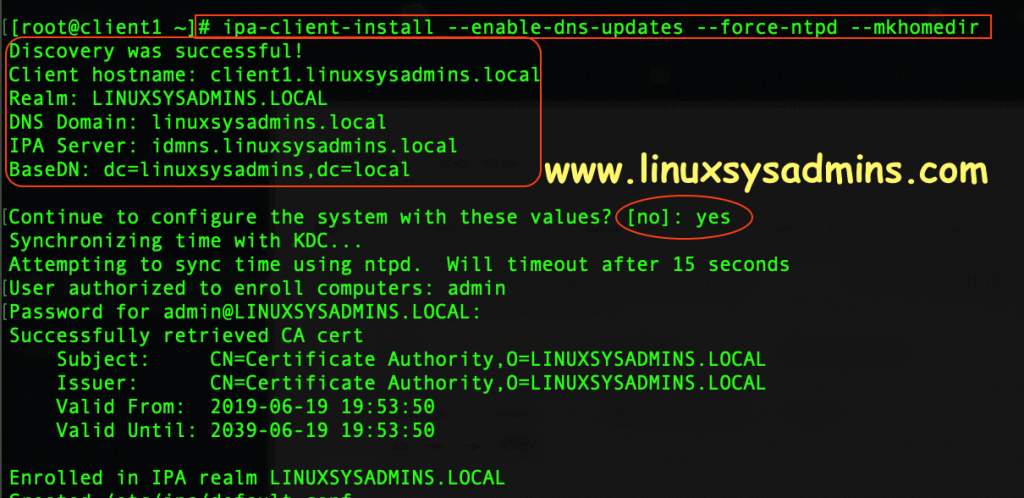
[root@client1 ~]# ipa-client-install --enable-dns-updates --force-ntpd --mkhomedir
Discovery was successful!
Client hostname: client1.linuxsysadmins.local
Realm: LINUXSYSADMINS.LOCAL
DNS Domain: linuxsysadmins.local
IPA Server: idmns.linuxsysadmins.local
BaseDN: dc=linuxsysadmins,dc=local
Continue to configure the system with these values? [no]: yes
Synchronizing time with KDC…
Attempting to sync time using ntpd. Will timeout after 15 seconds
User authorized to enroll computers: admin
Password for admin@LINUXSYSADMINS.LOCAL:
Successfully retrieved CA cert
Subject: CN=Certificate Authority,O=LINUXSYSADMINS.LOCAL
Issuer: CN=Certificate Authority,O=LINUXSYSADMINS.LOCAL
Valid From: 2019-06-19 19:53:50
Valid Until: 2039-06-19 19:53:50
Enrolled in IPA realm LINUXSYSADMINS.LOCAL
Created /etc/ipa/default.conf
New SSSD config will be created
Configured sudoers in /etc/nsswitch.conf
Configured /etc/sssd/sssd.conf
Configured /etc/krb5.conf for IPA realm LINUXSYSADMINS.LOCAL
trying https://idmns.linuxsysadmins.local/ipa/json
trying https://idmns.linuxsysadmins.local/ipa/session/json
Systemwide CA database updated.
Adding SSH public key from /etc/ssh/ssh_host_rsa_key.pub
Adding SSH public key from /etc/ssh/ssh_host_ecdsa_key.pub
Adding SSH public key from /etc/ssh/ssh_host_ed25519_key.pub
SSSD enabled
Configured /etc/openldap/ldap.conf
NTP enabled
Configured /etc/ssh/ssh_config
Configured /etc/ssh/sshd_config
Configuring linuxsysadmins.local as NIS domain.
Client configuration complete.
The ipa-client-install command was successful
[root@client1 ~]#Linux client Integrated successfully with IDM.
Check for AD accounts in IDM server
For a quick check just run “getent” to know whether it’s working as expected.
# getent passwd babin@winlinuxsysadmins.local
# getent passwd lonston@winlinuxsysadmins.local
# getent passwd raja@winlinuxsysadmins.localWe got the output for all AD accounts query.
[root@client1 ~]# getent passwd babin@winlinuxsysadmins.local
babin@winlinuxsysadmins.local::916001104:916001104:Bobin L.:/home/winlinuxsysadmins.local/babin:
[root@client1 ~]# getent passwd lonston@winlinuxsysadmins.local
lonston@winlinuxsysadmins.local::916001105:916001105:Lonston L.:/home/winlinuxsysadmins.local/lonston:
[root@client1 ~]# getent passwd raja@winlinuxsysadmins.local
raja@winlinuxsysadmins.local:*:916001110:916001110:Raja:/home/winlinuxsysadmins.local/raja:Login using AD account
Let’s try to login from my laptop to confirm whether AD account working on IDM client.
$ ssh raja@winlinuxsysadmins.local@192.168.107.101We are good at everything.
xxxxxxxxxx@xxxxxxxxxs-MacBook-Pro:~$ ssh raja@winlinuxsysadmins.local@192.168.107.101
Password:
Creating home directory for raja@winlinuxsysadmins.local.
-sh-4.2$
-sh-4.2$ pwd
/home/winlinuxsysadmins.local/raja
-sh-4.2$ ls -lthr
total 0
-sh-4.2$ ls -lthra
total 12K
drwx--x--x. 3 root root 18 Jun 25 21:57 ..
-rw-------. 1 raja@winlinuxsysadmins.local raja@winlinuxsysadmins.local 18 Jun 25 21:57 .bash_logout
-rw-------. 1 raja@winlinuxsysadmins.local raja@winlinuxsysadmins.local 193 Jun 25 21:57 .bash_profile
-rw-------. 1 raja@winlinuxsysadmins.local raja@winlinuxsysadmins.local 231 Jun 25 21:57 .bashrc
drwx------. 2 raja@winlinuxsysadmins.local raja@winlinuxsysadmins.local 62 Jun 25 21:57 .
-sh-4.2$
-sh-4.2$ id
uid=916001110(raja@winlinuxsysadmins.local) gid=916001110(raja@winlinuxsysadmins.local) groups=916001110(raja@winlinuxsysadmins.local),916000513(domain users@winlinuxsysadmins.local),916001108(winteladmins@winlinuxsysadmins.local) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
-sh-4.2$Verifying Conditional DNS forward from IDM Client
In our IDM/AD Server setup we have a DNS conditional forwarder, Let’s test one of “A record” created on AD/DNS server from IDM client.
For testing purpose created with two “A record” entry on AD as follows.
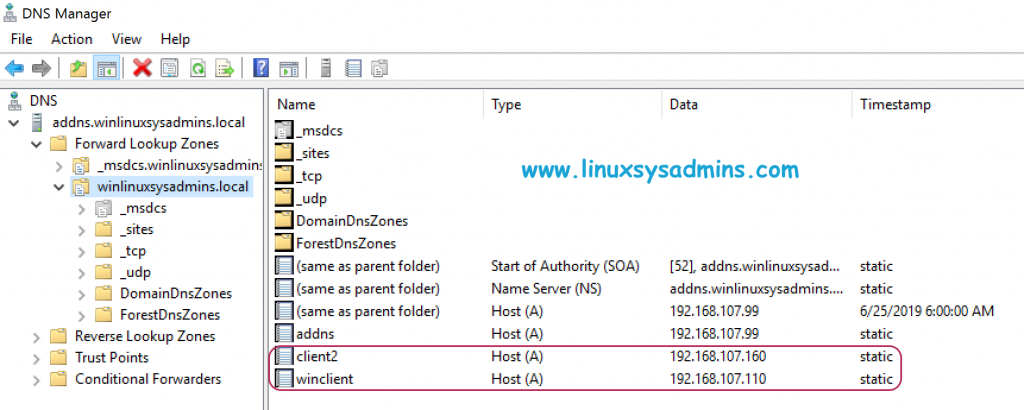
Run dig command to verify one of “A record” in AD servers.
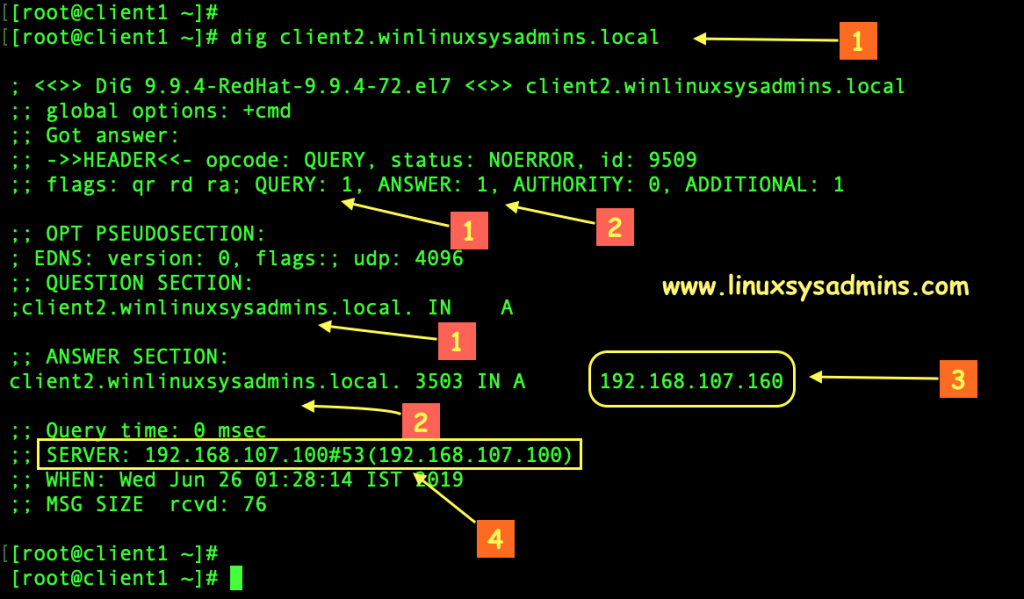
- Query/Question about client2.winlinuxsysadmins.local
- Answer received from IDM by resolving conditional forwarding on AD
- The IP address of the “A record” on AD/DNS (addns.winlinuxsysadmins.local)
- Getting Answer from IDM server (192.168.107.100|idmns.linuxsysadmins.local)
Or a simple check we can use the “host” command.
[root@client1 ~]#
[root@client1 ~]# host winclient.winlinuxsysadmins.local
winclient.winlinuxsysadmins.local has address 192.168.107.110
[root@client1 ~]#
[root@client1 ~]# host client2.winlinuxsysadmins.local
client2.winlinuxsysadmins.local has address 192.168.107.160
[root@client1 ~]#
[root@client1 ~]# host client1.linuxsysadmins.local
client1.linuxsysadmins.local has address 192.168.107.101
[root@client1 ~]#That’s it we have completed with a successful IDM & AD cross-forest trust.
Conclusion
Most of the critical production environment are looking for this solution, It’s been for a long time I’m working on this and finally documented each step for self-reference in the future. Hope this guide will help you in the current or future working environment. In case any improvement required in this article your feedback is most welcome in below comment section, Subscribe to our newsletter and stay with us to receive more articles based on Identity Management (IDM).
I was able to authenticate AD users on Linux. I was also able to set the sudo rules for AD group. Any modification in AD members takes hours to replicate on the Linux servers. Is there any frequency settings that might need to be set?
its really usefull to our organization. Thanks a lot sir!!!!!!!!!!!!!11