Table of Contents
Introduction
Linux Sudo configuration will escalate privileges for normal users. In this guide, we will create with a few users on our test server and assign them roles and walk through a few examples.
We have created 7 users on our test server. They are as follows.
[root@web04 ~]# tail -n 7 /etc/passwd
babin:x:1000:1000::/home/babin:/bin/bash
lonston:x:1001:1001::/home/lonston:/bin/bash
rajesh:x:1002:1002::/home/rajesh:/bin/bash
kamal:x:1003:1003::/home/kamal:/bin/bash
francis:x:1004:1004::/home/francis:/bin/bash
mon-team:x:1005:1005::/home/mon-team:/bin/bash
guest-user01:x:1006:1006::/home/guest-user01:/bin/bash
[root@web04 ~]#Assume below user’s assigned with some roles.
| User Account | Roles of Users |
| babin | SuperUser with all privileges. |
| lonston | Allowed to create logical volumes, filesystems and mount the filesystems. |
| rajesh | Only allowed to run a few selective commands. |
| kamal and mon-team | only allowed to read /var/log/messages, no write access or delete access. |
| francis | Users are allowed to patch the server and take a reboot during the weekend without the root password. |
| guest-user01 | User not allowed to run sudo su. |
Configure Linux Sudo for Users
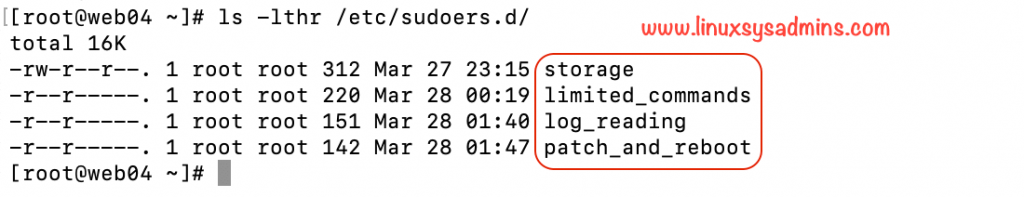
Let’s start with allowing users to some roles in sudo. While configuring the sudo we are not going to touch the main configuration file /etc/sudoers instead, we will create the new Sudo configurations under /etc/sudoers.d/. For your reference, we have shown in the below picture.
Understanding sudo Syntax is as follows.
user (host) = (user:group) commandUser_Alias USER_NAME = user1, user2, user3
Cmnd_Alias CMD_NAME = cmd1, cmd2, cmd3
USER_NAME (host) = (user:group) CMD_NAMEMost used sudo entry
Allow user “lonston” to run all commands without entering the root password. The most used sudo entry award goes to this one.
bobin ALL=(ALL) NOPASSWD: ALLProviding storage privilege for users
Let’s create a separate sudo configuration for storage privilege for a set of users.
# visudo -f /etc/sudoers.d/storageThe users under this STORAGE_ADMINS should have the privilege to create Physical volume, Volume group, logical volume and create a filesystem on them.
User_Alias STORAGE_ADMINS = lonston
Cmnd_Alias STORAGE_ACTS = /usr/sbin/fdisk, /usr/sbin/parted, /usr/sbin/partprobe, /usr/bin/mount, /usr/bin/umount, /usr/sbin/mkfs, /usr/sbin/pvcreate, /usr/sbin/vgcreate, /usr/sbin/lvcreate, /usr/sbin/pvs, /usr/sbin/vgs, /usr/sbin/lvs
STORAGE_ADMINS ALL=NOPASSWD:STORAGE_ACTSLet’s switch to lonston user to verify
[root@web04 ~]# su - lonston
Last login: Sat Mar 28 00:10:53 +04 2020 on pts/0
[lonston@web04 ~]$Now try to sudo su - into root user. You will not be allowed.
[lonston@web04 ~]$ sudo su -
[sudo] password for lonston:
Sorry, user lonston is not allowed to execute '/bin/su -' as root on web04.linuxsysadmins.local.
[lonston@web04 ~]$Once again run and verify fdisk -l which required root privilege. It will throw an error because you are not escalating the privilege with sudo.
[lonston@web04 ~]$ fdisk -l
fdisk: cannot open /dev/sda: Permission denied
fdisk: cannot open /dev/sr0: Permission denied
fdisk: cannot open /dev/mapper/centos-root: Permission denied
fdisk: cannot open /dev/mapper/centos-swap: Permission denied
[lonston@web04 ~]$Now, let’s escalate the privilege to the sudo.
[lonston@web04 ~]$ sudo fdisk -l
Disk /dev/sda: 16.1 GB, 16106127360 bytes, 31457280 sectors
Units = sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disk label type: dos
Disk identifier: 0x000acf12
Device Boot Start End Blocks Id System
/dev/sda1 * 2048 2099199 1048576 83 Linux
/dev/sda2 2099200 31457279 14679040 8e Linux LVM
Disk /dev/mapper/centos-root: 13.4 GB, 13417578496 bytes, 26206208 sectors
Units = sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disk /dev/mapper/centos-swap: 1610 MB, 1610612736 bytes, 3145728 sectors
Units = sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
[lonston@web04 ~]$Providing access to a Group
In case, if you need to provide sudo privilege for a group of users. Just put “%” at the beginning of the definition. For example
%iso_admins ALL=/usr/bin/mount /media/cdromLimiting users to selective commands
Limit users to execute privileged selective commands by configuring Linux sudo.
# visudo -f /etc/sudoers.d/limited_commandsUser_Alias OFFSITE_ADMINS = rajesh
Cmnd_Alias LIMITED_COMMANDS = /usr/sbin/useradd, /usr/sbin/groupadd, /usr/bin/passwd, /usr/bin/chage, /usr/sbin/userdel, /usr/sbin/groupdel
OFFSITE_ADMINS ALL=NOPASSWD:LIMITED_COMMANDSSwitch to Rajesh User
$ su - rajeshTry to add a new user without escalating privilege. You will get permission denied.
[rajesh@web04 ~]$ useradd summa
useradd: Permission denied.
useradd: cannot lock /etc/passwd; try again later.
[rajesh@web04 ~]$Run the same command with sudo. You will be good now.
[rajesh@web04 ~]$ sudo useradd summaLet’s try to create the password without sudo and with sudo.
[rajesh@web04 ~]$ passwd summa
passwd: Only root can specify a user name.
[rajesh@web04 ~]$[rajesh@web04 ~]$ sudo passwd summa
Changing password for user summa.
New password:
Retype new password:
passwd: all authentication tokens updated successfully.
[rajesh@web04 ~]$Check the age of created used without and with escalating the privilege.
[rajesh@web04 ~]$
[rajesh@web04 ~]$ chage -l summa
chage: Permission denied.
[rajesh@web04 ~]$[rajesh@web04 ~]$ sudo chage -l summa
Last password change : Mar 27, 2020
Password expires : never
Password inactive : never
Account expires : never
Minimum number of days between password change : 0
Maximum number of days between password change : 99999
Number of days of warning before password expires : 7
[rajesh@web04 ~]$Allow user to read logs
To allow some user to read any logs it can be accomplished by defining in sudo configuration.
# visudo -f /etc/sudoers.d/log_readingAppend with below User alias and command alias.
User_Alias INCIDENT_TEAM = kamal, mon-team
Cmnd_Alias LOG_READING = /usr/bin/less /var/log/messages, /usr/bin/more /var/log/messages, /usr/bin/view /var/log/messages
INCIDENT_TEAM ALL=NOPASSWD:LOG_READINGTo verify the same
[root@web04 ~]# su - kamal
Last login: Sat Mar 28 01:38:20 +04 2020 on pts/0
[kamal@web04 ~]$[kamal@web04 ~]$ more /var/log/messages
/var/log/messages: Permission denied
[kamal@web04 ~]$ When we use sudo it is possible to read the /var/log/messages log.
$ sudo view /var/log/messagesGrant access to Patch and Reboot
Few users are assigned to patch and reboot the servers during the weekend. Let’s define the Linux sudo configuration in a separate file.
# visudo -f /etc/sudoers.d/patch_and_rebootAppend with the below sudo entry.
User_Alias PATCH_AND_REBOOT = francis
Cmnd_Alias PATCHING = /bin/rpm, /usr/bin/yum, /usr/sbin/reboot
PATCH_AND_REBOOT ALL=NOPASSWD:PATCHINGLinux sudo output for reference
[francis@web04 ~]$ yum update
Loaded plugins: fastestmirror
You need to be root to perform this command.
[francis@web04 ~]$
[francis@web04 ~]$ reboot
User root is logged in on sshd.
Please retry operation after closing inhibitors and logging out other users.
Alternatively, ignore inhibitors and users with 'systemctl reboot -i'.
[francis@web04 ~]$
[francis@web04 ~]$ systemctl reboot -i
==== AUTHENTICATING FOR org.freedesktop.login1.reboot-multiple-sessions ===
Authentication is required for rebooting the system while other users are logged in.
Authenticating as: root
Password:
[francis@web04 ~]$By running with sudo it will work.
# sudo yum update -y
# sudo rebootNow we are good with patching and taking a reboot by assigning Linux sudo privilege for a normal user.
Limit user to access Applications
For instance, your application team has three developers. And your application is hosted under /opt/application/ so its binary files will be under /opt/application/bin/ and your team needs full control for all commands related to your application, In such scenario below sudo entry will help for you.
Cmnd_Alias APP_SERVICE =/opt/application/bin/*
User_Alias APP_ADMINS = user1, user2, user3
APP_ADMINS ALL=NOPASSWD:APP_SERVICE
APP_ADMINS ALL=(ALL) NOPASSWD: /bin/su - appuser,/usr/bin/su - appuserThese users are normal users, to perform any modification on their code they need to switch to the application user, by appending the last line they are allowed to switch to their application without prompting application users password.
Disable sudo su for users
The restricted users are not allowed to run switch user (su).
# visudo -f /etc/sudoers.d/restrictedBy appending below config we are good with it.
guest-user01 ALL = ALL, !/bin/suFor time being above are the Linux Sudo examples, which will update frequently.
Conclusion
Linux Sudo escalates the privilege to root and gain the superuser privilege access for normal users, There are more examples upcoming on this same topic in future. Subscribe to our newsletter and stay with us.